I’ve written extensively on awareness and prevention to the point that certain topics become repetitive. However, I’ve not delved into the cost and ramifications that result from a data security breach.
It is very difficult to quantify the true cost of a data breach; the numbers vary by industry, individuals, and regulations. Fortunately, The Ponemon Institute releases an annual report from a survey sent to industry professionals where it breaks down responses from individuals who experienced a data breach incident at their organization. 3,200 individuals from 524 breached organizations across 17 countries/regions and 17 different industries were interviewed in 2020.
Unfortunately, the report does not highlight the cost that an individual faculty member or a research group may suffer from a data security breach.
The good news for the Education sector is, that the average total cost of a breach went down 20.2% in 2019-2020, compared to the previous year. However, the cost of a breach remains significant and averages institutions millions in losses.
Some of the report’s key findings indicate that:
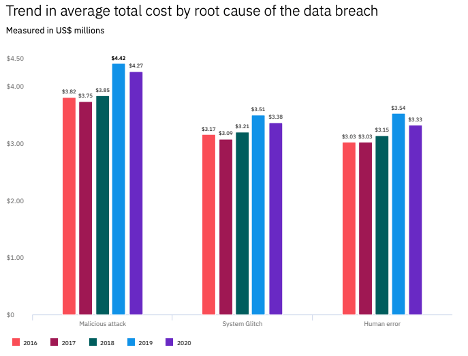
- 52% Share of breaches caused by malicious attacks, at an average cost of $4.27 million
- 19% Share of malicious breaches caused by compromised credentials (19%) and cloud misconfiguration (19%)
- $4.43million Average cost of breaches caused by nation-state attackers, responsible for 13% of malicious breaches
The report also breaks down the breaches by root cause: Malicious Attacks (52%), System Glitches (23%), and Human Error (23%).
The cost associated with the root cause also went down from previous years.
Time!
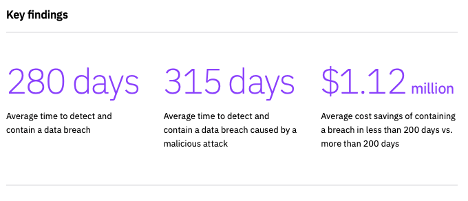
In previous years, this research has shown that the faster the data breach can be identified and contained, the lower the costs. The average time to identify describes the time it takes to detect that an incident has occurred. The time to contain refers to the time it takes for an organization to resolve a situation once it has been detected and ultimately restore service. The time elapsed between the first detection of the breach and its containment is referred to as the data breach lifecycle. These metrics can be used to determine the effectiveness of an organization’s incident response and containment processes. For the first time, this year’s study examined the impact of security automation on the direction of the data breach lifecycle.
Data Breach Violation Penalties
- HIPAA Violation Penalties:
- Tier 1:Minimum fine of $100 per violation up to $50,000
- Tier 2:Minimum fine of $1,000 per violation up to $50,000
- Tier 3:Minimum fine of $10,000 per violation up to $50,000
- Tier 4:Minimum fine of $50,000 per violation
- FERPA Violation Penalties:
- The most extreme consequence for violating FERPA is the loss of federal education funds.
- Personal Identifiable Information (PII) Violation Penalties
- Unauthorized Disclosure Violation Deliberate, unauthorized disclosure of PII to others. Infractions involving PA violations (willful disclosure of PA information to unauthorized recipient(s)) may result in criminal prosecution under the PA. The potential criminal penalties consist of incarceration and monetary fines up to $5,000.
- Unauthorized Access Violation Deliberate, unauthorized access to or solicitation of PII. Infractions involving PA violations (requests for access to PA information under false pretenses) may result in criminal prosecution under the PA. The potential criminal penalties consist of incarceration and monetary fines up to $5,000.
Individual Costs
Each individual case for a data breach is unique, therefore putting a monetary figure relating to a data breach is very difficult. Whatever the case, we have to consider TIME. How valuable is your time when a device or multiple devices have been compromised? How were your devices compromised? Was it ransomware or other malware, social engineering (Phishing), equipment/software failure, physical theft of equipment? A data breach can lead to reputational damage.
Malware/Ransomware
Throughout my years of providing desktop support, I found that a security breach usually takes an average of 72hrs. of downtime for an individual device. This includes diagnostics, reformatting a computer to bring it back to a clean working condition, and data recovery.
In addition to that, if you have regulated data that is compromised you will have to account for each individual record. The fines vary by institution, but the average fine is $1000 per individual record compromised.
Now, if the issue is Ransomware, hopefully, you haven’t disbursed any payment to the criminals in order to recover your data. If not, that’s an extra cost added to your time – and pocket!
$$$ = Your time + Diagnostics time + Data violation penalties x (No. Records compromised) x number of devices compromised + Reputational Damage.
Social Engineering
Social Engineering is perhaps the most complicated data breach to mitigate. Depending on each case, you might end up spending time disputing claims with different organizations.
- Were your passwords or other credentials compromised? If so, do you use the same password for all your other accounts? The cost associated with this will be your time, and any financial losses if your bank/credit card accounts were the target of the social engineering attack. Included in this category Sextorsion, the fake IT Support requests, the fake invoices.
- Was your social security number compromised? The cost associated with this case will be your effort to put a security block on your social security number, contacting credit bureaus in order to put a social security block to prevent new lines of credit, loan applications, etc. from being open under your name. Under this category, I include the COVID-19 Unemployment scams and IRS Scams.
- Were you a victim of the “Gift Card” scam? The cost associated with the gift card amount that was requested by the criminal posing as a colleague, friend, or family member.
$$$ = Your time + diagnostics time + amount stolen + data violation penalties
Learn to identify a phishing attempt.
Equipment/Software Failure
How frustrating it is when a computer/device stops working all of the sudden! The hard disk crashed, a USB Key no longer works, the computer died… luckily, there is a data recovery plan in place; good known backups exist, data can be recovered whether from an external backup drive or a cloud backup account – we have been saved by being proactive! The only worry to have is how much it’ll cost and how long it will take to replace the damaged equipment.
But if the data recovery plan is non-existent it can be a lengthy and sometimes painful process – your data may not be recoverable. Research, theses, photographs, videos, audio all gone in a split second.
Data recovery is not cheap! Anecdotally, from an incident in 2017, data recovery from one 4GB USB Memory drive ended up costing $1400, with a turnaround response of 1 week. The prices go up if you want a faster turnaround response, and it’s not 100% certain that one will get all the data recovered.
Software failure (let’s call it misconfiguration) is another costly recovery process. Do you host a database on a server? Do you have a website running JavaScript, PHP or other code? Do you ensure that your code is in tip-top order? Are your firewall rules actively doing what they are supposed to do? Did you know that having unsecured, out-of-date code can leave you vulnerable to targeted attacks? Malicious actors are always scanning and looking for vulnerabilities, and open (vulnerable) database/web servers are the most targeted, and the easiest way to steal data.
The costs associated with software misconfigurations on a server are that not only your website might be defaced, but your data records can also be stolen – it’s happened to Facebook, Yahoo, and Experian (to name a few notable cases). Imagine the reputational damage, the financial cost to pay consultants to fix and mitigate any issues with your code, and the cost of paying hefty fines – if the records exposed are PII or HIPAA regulated.
And then there are the outdated software applications. These are the ones such as an outdated Operating System, whether MacOS, Windows, Linux, etc.; an outdated web browser, MS Office, or even Adobe products. If those applications are outdated, devices are more prone to a localized breach or a damaged computer – and they apply to mobile devices as well. In any case, a breach of this type opens the door to threat actors to potentially have access to your most precious data, and sometimes you don’t even know that your device has been compromised until it is too late.
If you participate in the use of CrashPlan PRO for Northwestern University, you can learn how to check if your backup is in an optimal state, and also you can learn how to restore files.
Physical Theft
Perhaps the most obvious event that makes one panic and makes one think more consciously about the fact that the data is no longer in our possession. However, do you know what to do (besides calling the police) if your computer is lost or stolen?
After such an event, this is a great use case for the University Security and Management Systems, such as KACE and Jamf. Our university IT units have the capability of locking your computer, erasing the data, and even potentially locating your device – that is, if your computer was configured using the University Management Systems. These tools help us protect our identities; they assist us to collaborate with the authorities, and these tools also allow us to prevent someone from having direct access to our data by way of encryption.
Having a good backup strategy also assists you in recovering your data, even if your device is lost forever. The university provides an automated backup and recovery tool (Crashplan PRO) for university-owned devices.
However, if you don’t have a device that is part of a managed environment, such as your personal devices, you can take simple steps to ensure that in the event that you lose your data whether by social engineering scams, malware, hardware failure, or theft.
Data Backup and Data Recovery Strategy
- Determine what to backup (full system vs. individual files)
- Determine whether you want to implement an automated backup tool, e.g., Carbonite
- Invest in an Antivirus Software – I personally recommend Sophos Antivirus
- Document the institutions that you need to contact in the event of data loss
- Social Security Office
- Credit Bureaus
- Financial and Banking Institutions
- HR Department(s)
- Utility companies
- The Federal Trade Commission
- Save files consistently
- Save files to multiple locations (Box, Google Drive, Dropbox, etc.)
- Test your data recovery plan
- Ensure that your passwords are stored in a safe location (e.g., LastPass)
- Verify that your data backup is in a current good state
- Ensure that you know how to restore files
Data privacy and data security concerns will only increase year after year, institutions are improving ways to mitigate data breaches and malware attacks with limited budgets and personnel. But in the end, even the most expensive and well-configured tools will not prevent an individual from (unsuspectedly) opening the door to a criminal organization. The risks are even higher with the increase of work-from-home environments, where the security management falls primarily on the individuals rather than the institutions.
Finally, I’ll leave you with two questions to ponder: What is your cybersecurity posture? How much would a data breach cost you?